Social engineering audit
Even if your systems are secure, when the user is the weak link… everything goes down.
What is a Social Engineering attack?
Social engineering attacks manipulate and deceive employees to obtain confidential information to breach the company’s security.
People, the weak link in cybersecurity.
Through a social engineering audit, your organization will not only be able to have a report of its current status in terms of social engineering breaches, but will also have specific training to make users aware of the existing risks.
%
Of the cyberattacks that are successful occur due to carelessness or human error.
Real cases of social engineering attacks in different industries
Banking
Since the workers thought the swindler was a special client and were friends with him, they gave him access to the vaults where the diamonds were kept, an opportunity that the thief did not miss.
It should be noted that the stolen area had been equipped with a security system costing more than 1 million euros.
Banking
| In 2007 a thief managed to steal 21 million euros in diamonds from a bank in Belgium using only social engineering. He created an account at the bank with a stolen passport, and gained the trust of the employees for a year by posing as a successful businessman. He frequently visited the bank and gradually gained the trust of the employees (with small details such as boxes of chocolates), until he became friends with the staff.
Since the workers thought the swindler was a special client and were friends with him, they gave him access to the vaults where the diamonds were kept, an opportunity that the thief did not miss. It should be noted that the stolen area had been equipped with a security system costing more than 1 million euros. |
 |
Press
That tweet was only active for 3 minutes, however in that time the Wall Street stock market dropped 150 points, about 136 billion before it recovered near its previous level. This email could have had a devastating effect on the U.S. economy, and properly managed, could have netted the attackers a large amount of money through short-term trading in the stock market.
The attack was done by sending a spear phishing email targeting Associated Press employees, as if it came from other employees of the same company, although in reality the attack was sent from a group called the Syrian Electronic Army. Within the email the sign that it was a phishing email was the fact that the name of the email sender did not match the name that appeared in the email signature.
Press
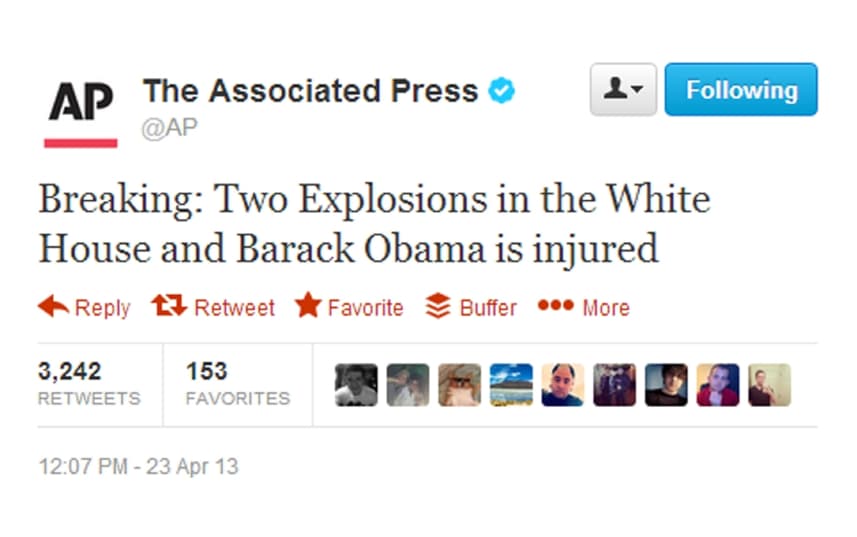
| In 2013 the Associeted Press Twitter account, an account notable for its high impact in the United States with over 1.9 million followers, and a tweet was posted stating that the White House had been bombed and President Obama was injured in the blast.
That tweet was only active for 3 minutes, however in that time the Wall Street stock market dropped 150 points, about 136 billion before it recovered near its previous level. This email could have had a devastating effect on the U.S. economy, and properly managed, could have netted the attackers a large amount of money through short-term trading in the stock market. The attack was done by sending a spear phishing email targeting Associated Press employees, as if it came from other employees of the same company, although in reality the attack was sent from a group called the Syrian Electronic Army. Within the email the sign that it was a phishing email was the fact that the name of the email sender did not match the name that appeared in the email signature. |
 |
Retail
He accomplished this by simply walking into the stores confidently, dressed in the Walmat uniform, and claiming that he was conducting an inventory of the stores before the general managers conducted a post-holiday inspection. Store employees believed his story and granted him access to the restricted areas he needed, on some occasions the store manager even gave him a hug of thanks, although that opinion changed when he realized what the young man had actually done.
Retail
| In 2013 a 17-year-old was fired from his job at Walmart after stealing money. Following this and taking advantage of the fact that he still had his company uniform, he went to 3 other Walmart locations and stole another $30,000.
He accomplished this by simply walking into the stores confidently, dressed in the Walmat uniform, and claiming that he was conducting an inventory of the stores before the general managers conducted a post-holiday inspection. Store employees believed his story and granted him access to the restricted areas he needed, on some occasions the store manager even gave him a hug of thanks, although that opinion changed when he realized what the young man had actually done. |
 |
Software
As a result of the Bit9 attack, the cybercriminals managed to steal the certificates used by Bit9 for code signing, allowing them to create malware that looked like legitimate Bit9-developed software, and attack organizations that use and trust Bit9-signed software.
Software
| In 2013 the software company Bit9 was hacked using the “watering hole attack” tactic, which involves infecting websites that the target is likely to visit, and waiting until their malware successfully infects a device from that company. For example, in this case the attacker could have infected a website such as Stack Overflow, which programmers frequently visit to ask or answer programming-related questions.
As a result of the Bit9 attack, the cybercriminals managed to steal the certificates used by Bit9 for code signing, allowing them to create malware that looked like legitimate Bit9-developed software, and attack organizations that use and trust Bit9-signed software. |
 |
Cinema
The cyberattack began with a phishing email posing as Apple to several Sony executives, asking them to verify their credentials. Using the LinkedIn profiles, the attackers determined their likely login credentials for the Sony network, and identified at least one executive who used the same password for both his Apple and Sony accounts. With those credentials the credentials managed to steal 100 terabytes of confidential company and employee information.
Major U.S. theater chains suspended showing the movie following threats made by cybercriminals against theaters showing the film, and Sony Pictures suspended the film’s release.
Cinema
| In 2014 Sony pictures was preparing to release the movie “The Interview,” a comedy about two men training to assassinate the leader of North Korea. In response North Korea threatened terrorist attacks against movie theaters and allegedly hacked Sony Pictures’ computer networks (although North Korea denied involvement).
The cyberattack began with a phishing email posing as Apple to several Sony executives, asking them to verify their credentials. Using the LinkedIn profiles, the attackers determined their likely login credentials for the Sony network, and identified at least one executive who used the same password for both his Apple and Sony accounts. With those credentials the credentials managed to steal 100 terabytes of confidential company and employee information. Major U.S. theater chains suspended showing the movie following threats made by cybercriminals against theaters showing the film, and Sony Pictures suspended the film’s release.
|
 |
Politics
This was achieved through a spear phishing email where Russian cybercriminals sent an email that appeared to be from Google, warning of unusual activity in their email accounts, and inviting the recipient to click on a link to change the password.
Once the attackers had the correct passwords, they had access to their targets’ email accounts, allowing them to download and leak thousands of emails containing information sensitive to the Clinton campaign.
Politics
| In 2016, during the presidential election, a variety of sites leaked more than 150,000 stolen emails from 12 Hillary Clinton campaign staffers.
This was achieved through a spear phishing email where Russian cybercriminals sent an email that appeared to be from Google, warning of unusual activity in their email accounts, and inviting the recipient to click on a link to change the password. Once the attackers had the correct passwords, they had access to their targets’ email accounts, allowing them to download and leak thousands of emails containing information sensitive to the Clinton campaign. |
 |
There are two types of companies: those that have been hacked and those that do not yet know they have been hacked.
Many companies believe that an antivirus or firewall protects them enough, since cybercriminals have never specifically attacked them and never will because they are not interesting for them, but the reality is that all companies can be victims of cyberattacks, and sometimes even have been without the company becoming aware of it.
By performing a social engineering audit in your company you will not only detect and understand the vulnerabilities, but also how to solve these vulnerabilities, a prioritization of these depending on the level of criticality, and recommendations on security policies.
Beware! Small businesses also receive cyber-attacks.
%
Of the attacks are targeted at SMEs.
What do I get by performing a social engineering audit?
✅ Identify vulnerabilities in people in your organization.
✅ Instructions for resolving vulnerabilities.
✅ Knowledge of the company’s risk situation.
✅ Preserving the confidentiality of data.
✅ Protection against loss and leakage of information.
✅ Increased security in access to resources.



