Exodus spyware succeeds in infecting IOS users
9/Apr/2019Vulnerabilidades, Vulnerabilities
Exodus spyware succeeds in infecting IOS users
9/Apr/2019Vulnerabilidades, Vulnerabilities
Computer security researchers at Lookout have detected an iOS version of the Exodus spyware, which until now only affected Android.
On iOS Exodus is not as dangerous as its Android variant, where it can gain root access to affected devices. However, on iOS it can steal contacts, photos, videos, voice memos, and even your location, without the user even realizing it.
How has Exodus breached IOS security?
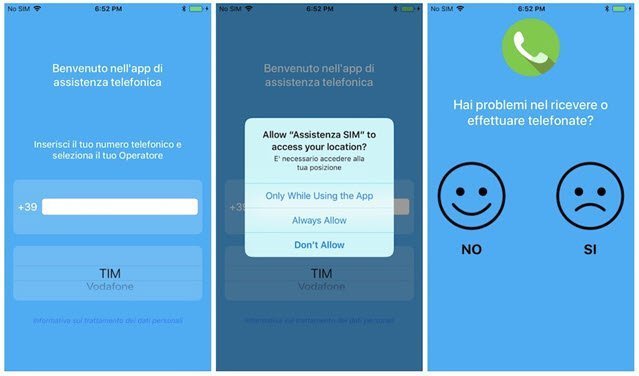
Apple’s App Store has stricter security restrictions than the Google Play Store, but unlike its Android variant (where Exodus was distributed through the Google Play Store), the iOS version has been distributed outside the App Store, gaining the trust of users by impersonating Italian and Turkish mobile operators through phishing websites (websites that imitate the original ones of those operators).
Apple restricts the direct installation of applications outside the App Store, but this time to allow the installation of Exodus, when the fake operator websites where the malware was distributed ask users to install an enterprise certificate from the Apple Developer Enterprise, which allows companies to distribute their own internal apps directly to their employees without having to publish them on the App Store. Clearly this is a violation of Apple’s enterprise certificate guidelines, which is why Apple has withdrawn the certificates through which the Apps were distributed.
What is the origin of Exodus?
Exodus is the original name of the app designed for Android. This app contains surveillance software created by Connexxa, and widely used by some Italian government entities. The Android version of this app was installed on hundreds of devices, sometimes voluntarily, sometimes without the users’ knowledge.
On Android, Exodus can have root access to affected devices, so it can be much more dangerous.
How to avoid becoming a victim of Exodus?
After the discovery of this spyware, Apple revoked the company certificates, preventing malicious applications from being installed on new iPhones, and running on previously infected devices.
Still, if you are an iPhone user and want to avoid being a victim of such attacks in the future, what you should do is install only apps from the App Store, which have gone through Apple’s security process, and not rely on external apps.
You never know what apps that haven’t gone through Apple’s security process might be hiding….

Related Articles
Sofistic, Exabeam’s Growth Award
Exabeam recognizes Sofistic's background and growth in cybersecurity In the dynamic world of cybersecurity, distinction and recognition are not only a reflection of past achievements, but a promise of what is about to come. That's why we are proud to have been...
Sofistic obtains the new Microsoft Solutions Partner Security Certification
After obtaining Microsoft solutions Partner Modern Work, Sofistic has recently obtained the Microsoft Solutions Partner Security certification, demonstrating the successful adaptation to the new requirements established by the technological giant. One of the first...
Sofistic ranks among Microsoft’s top partners with Modern Work certification
Sofistic, among Microsoft’s top Modern Work Certified partners




0 Comments